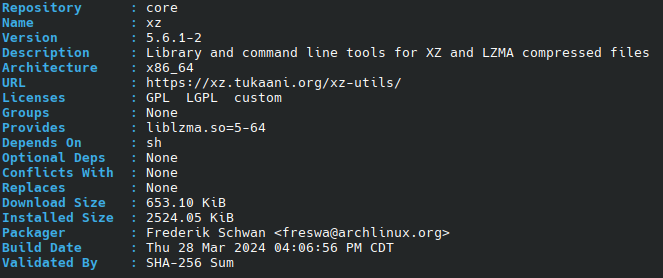
https://arstechnica.com/security/20...nux-utility-breaks-encrypted-ssh-connections/
View: https://gist.github.com/thesamesam/223949d5a074ebc3dce9ee78baad9e27
Extremely nasty. Expect to be seeing more of this in headlines the coming days, I guess.
And the deets on the discovery as a bonus; from the man himself.
View: https://mastodon.social/@AndresFreundTec/112180406142695845
View: https://gist.github.com/thesamesam/223949d5a074ebc3dce9ee78baad9e27
Extremely nasty. Expect to be seeing more of this in headlines the coming days, I guess.
And the deets on the discovery as a bonus; from the man himself.
View: https://mastodon.social/@AndresFreundTec/112180406142695845
![[H]ard|Forum](/styles/hardforum/xenforo/logo_dark.png)